 Are you worried about the security of your Computer and your data? Want a worry free computing experience?
Are you worried about the security of your Computer and your data? Want a worry free computing experience?
Perry Hall Computing offers a Total Care plan
With our Our Total Care Plan you will get
- Managed Anti-Virus software
- Unlimited free virus removals
- Reports are run every hour to check for infections, Windows services stopped, Hard Drive space and health, and other critical components
- Daily update checks for Windows and third party security updates (java, flash etc)
- Daily automated mini-tune up to keep your customer’s computers running smooth
- Sneaker ware Prevention – Automatically chooses “No” during software installation for additional software (toolbars, adware etc)
- Website Filtering – Blocks known attack sites, and other categories the customer requests such as Adult sites etc..
Only $21.00 Per month be safe , secure and have your computer running at peak performance
You E-mail has been Hacked- What Should You Do
 Almost everyone has had this happen, you get a text or an email from someone and they say “you’ve been hacked”. You begin to panic and wonder how this happened to YOU!?!?
Almost everyone has had this happen, you get a text or an email from someone and they say “you’ve been hacked”. You begin to panic and wonder how this happened to YOU!?!?
Reality: Someone May Be Snooping Your Network
 Since 1999 we have been offering onsite computer repair I’ve come across countless open Wifi networks. If you use a laptop or other wireless device in an urban area you’ve seen them too. Some networks are set up this way to allow others in the neighborhood to share an Internet connection (though your ISP may frown on this). Others because the person lives far enough away from anyone that they believe distance protects them from hackers or the like. After all, sometimes your Wifi signal doesn’t reach much further than the walls of the house.
Since 1999 we have been offering onsite computer repair I’ve come across countless open Wifi networks. If you use a laptop or other wireless device in an urban area you’ve seen them too. Some networks are set up this way to allow others in the neighborhood to share an Internet connection (though your ISP may frown on this). Others because the person lives far enough away from anyone that they believe distance protects them from hackers or the like. After all, sometimes your Wifi signal doesn’t reach much further than the walls of the house.
The problem is that when your network is open pretty much everything you do on your computer is visible to anyone else on that network, if they know how to look for it. And, while you may not be able to see your wireless network very far beyond the borders of your home, most of the people who want to snoop on your connection have much more powerful antennas that allow them to connect over great distances. It’s also not just your data that you need to worry about. You can also be hurt by what the person connecting to your wireless does with your Internet connection.
The good news is that securing your wireless network is a fairly easy and straight forward process. The reality is that most people who want to do bad things with your wireless connection are looking for an easy score. They will likely see that your network is protected and just move on to greener pastures.
Perry Hall PC Repair Wireless Security Service Special
For Only $89 We will come to your home and secure your wireless network to keep your network activity safe from prying eyes. With an Un-secured wireless network your Banking activity, online purchase information is up for grabs
$89 is a small price to pay for peace of mind
Your Worst Computer Nightmare – CryptoLocker
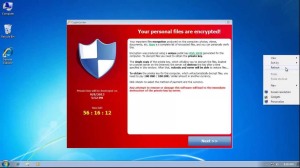 Ransom ware is a variety of malware that, once it infects its host-machine, at least says it’s encrypted the data on or locked its victim’s machine in some other way. The malware then informs the infected user that he or she must pay a ransom in order to unlock their files. Of course, there is never any guarantee whatsoever that paying the ransom will unlock anything. In this case the Cryptolocker really carries out the threat, The virus encrypts files stored on local hard drives and mounted network drives using public-key cryptography, and then displays a message saying that the files will be decrypted by a 2048-bit RSA key pair if a fee is paid through an anonymous payment service by a specified deadline, beyond which decryption is no longer possible. There is no way to decrypt the key.
Ransom ware is a variety of malware that, once it infects its host-machine, at least says it’s encrypted the data on or locked its victim’s machine in some other way. The malware then informs the infected user that he or she must pay a ransom in order to unlock their files. Of course, there is never any guarantee whatsoever that paying the ransom will unlock anything. In this case the Cryptolocker really carries out the threat, The virus encrypts files stored on local hard drives and mounted network drives using public-key cryptography, and then displays a message saying that the files will be decrypted by a 2048-bit RSA key pair if a fee is paid through an anonymous payment service by a specified deadline, beyond which decryption is no longer possible. There is no way to decrypt the key.
US-CERT issued an advisory this week warning businesses and consumers of the risks presented by CryptoLocker, which has been on the radar of security experts since late October. US-CERT said infections are on the rise and urge victims not to pay the ransom, instead report it to the FBI’s Internet Crime Complaint Center.
How the virus works – What does it steal from you? Who does it Target?
CryptoLocker installs itself to the Documents and Settings folder on your system and then proceeds to search for specific file types like Microsoft Word Docs or Adobe PDFs. It applies an asymmetric encryption which requires both a public and private key to unlock. The public key is stored in the virus itself and is used to encrypt the files. The private key is hosted on the hacker’s server.
We have noticed a high infection rate here in Baltimore County as well as the surrounding metro Baltimore area. This is serious business for these thugs and for the first time this type of attack is being considered organized crime.
How do I get it?
- As an email sent to company addresses pretending to be from customer support from FedEx, UPS, DHL, etc. The virus is attached to the email, usually labeled as a tracking number.
- In PDF documents that are attached to emails.
- Via hacked websites that can exploit computer vulnerabilities to install the infection.
- Through Trojans that pretend to be programs you need to download in order to watch videos online.
Some versions of CryptoLocker are reportedly capable of affecting not only local files but also files stored in Removable Media such as USB sticks, external hard drives, network file shares and some cloud storage services that are able to sync local folders with online storage. The US-CERT notification also warns that the malware can jump from machine to machine within a network and advises that infected users remove affected machines from their networks immediately.
Can Baltimore PC Repair remove the virus?
 The techs and engineers here at Perry Hall PC Repair have had success with removing the virus but at this point it is impossible to retrieve the encrypted files so honestly the best practice is to wipe the hard drive and start over.
The techs and engineers here at Perry Hall PC Repair have had success with removing the virus but at this point it is impossible to retrieve the encrypted files so honestly the best practice is to wipe the hard drive and start over.
IMPORTANT SAFETY INFORMATION
- Beware of attachments – Always look at your attachments. If you get an email with an attachment from any sender you don’t personally know don’t open it. If you get an attachment from people you do know, but it isn’t something they would normally send, don’t open it. For all other attachments, try confirming that the file attached is in fact legitimate by asking the sender.
- Backup your data – Be sure to always backup your data on a regular basis. If you backup files on a daily or even weekly basis and are infected, you can easily wipe your hard drives and start again without losing much in the way of data.
- Know what to do if infected – If you are infected the first thing you should do is disconnect from the network to limit the chance of the virus spreading to other systems. If you have backed up your system and data, you can probably revert your system. If not, your best plan of attack would be to contact us to see if we can help, as we may be able to get around the encryption or even delete it
Shop Safely This Holiday Season 4 Quick Tips
 Even though Cyber Monday, and Black Friday may mark the high points of the holiday shopping season, but they are by no means the end of it. In a still struggling economy, with everyone searching for value, consumers will encounter technology deals that might seem too good to be true.
Even though Cyber Monday, and Black Friday may mark the high points of the holiday shopping season, but they are by no means the end of it. In a still struggling economy, with everyone searching for value, consumers will encounter technology deals that might seem too good to be true.
As reported by the Dow Jones news wire, Online shopping may well top $1 billion dollars on a single day this year. With more and more consumers willing to spend money Online, sales will rise, but so will the risk of exposure to some sort of scam or cyber-crime right alongside those fabulous deals.
So, how can you avoid being taken advantage of?
There are many ways to keep yourself, your privacy, and your money safe this holiday season. But, as the countdown to Christmas grows shorter, many of us abandon our common sense in the desperate pursuit of that one great gift or that one fantastic deal.
Therein lies the problem. The number one way to guard against Online scams is to employ some common sense.
For example, many of us will go to extreme lengths to save a few dollars. This often includes venturing off the ‘beaten path’ and looking outside the major retailers on Online auction or classified sites such as E-Bay or Craigslist, which the Better Business Bureau has cautioned against. While many of the deals offered on such sites are perfectly legitimate, the likelihood of stumbling into a scam is far greater on these sorts of sites.
Tip #1
If a deal seems too great, it probably is, especially if it’s from an individual user or a ‘minor’ retailer. Be suspicious of any deal or sale that you can’t believe is real. Maybe you’ve found the best buy of the season, but it’s more likely that you’ve stumbled into a scam set up to defraud you and steal your money or information.
It’s also important to remember that anyone you do business with Online knows more about Internet commerce — and its dangers — than you do.
Tip #2
Is to do some research about any Online vendor you’re considering making a purchase from. Some vendors believe quality customer service goes hand in hand with turning a profit.
Tip #3
Consumers would also be wise to investigate other forms of payment, such as Papal or Bill Me Later, a Papal service. While alternative methods may not offer the convenience of credit cards, they may provide more security against potential scams and those who know how to abuse the system.
Regardless of where and when you shop Online Be cautious
Tip #4
For the online shopper: understand your credit cards. Broker and other merchants like him, were able to take advantage of customers because of the rules set up by the credit cards those customers use.
With credit card purchases being the dominant form of Online shopping, it’s vital that consumers know the policies of the cards they use and what recourse they have should those policies be abused.
Never Get A Virus Again –
 Install a Good Antivirus Software and Keep it Up to Date
Install a Good Antivirus Software and Keep it Up to Date
If you don’t have antivirus software installed, then you need to get on this right away. I would highly recommend Vipre Anti-Virus If you are looking for a good antivirus. The second part of this is that you need to keep this software up to date and you need to run scans regularly. Most good antivirus software packages will automatically update themselves. However, it is a good idea to check that this is happening. When it comes to scanning, it is a good idea to scan every week or so. By keeping your virus protection software up to date and by scanning often, you can make sure you catch any threats before they can wreak havoc on your PC.
Be Careful When Opening and Clicking Links Within Emails
Opening a bad attachment or directly clicking on a virus in an email are two really common ways to get a virus. There are quite a few ways to avoid this. First, be really careful opening emails that have attachments from people you don’t know. Second, if you open an email, you don’t recognize the sender, and the email itself really doesn’t make sense, then don’t click on any of the links in the email. In this case, it is best to just delete the email and move on. Last, if you are not with a solid email provider like G Mail, Yahoo Mail, etc, then you may want to think about switching. These services do a great job of filtering out any viruses before they even get to your inbox.
Be Careful When Browsing the Internet
Another really common place to get a virus is from a bad website. We have all been there, we have clicked on a link or a result in Google search and we end up at a website that just doesn’t look trustworthy. This site is trying to get you to download stuff, has tons of popups, and won’t even let you go back. In most cases, you are still OK. However, what you do next may determine if you get a virus or not. First, see if you can go back or even see if you can close out the browser window. If it doesn’t let you, you can try to close any popups or notifications using the “X” or the cancel button. If you still can’t get away from the bad site, you can use the task manager by pressing CTRL+ALT+DEL to manually close your browser task. The big key is that whatever you do, don’t allow your browser to download anything. Most browsers today will ask if you are sure that you want to continue with a download. This is where you make your last stand against the virus.
To go along with this, it is best to just avoid certain types of sites. First of all, avoid public torrents and public torrent sites. These are well-known virus farms. You may also want to be careful around any type of adult sites or any low quality streaming sites. I am not talking about YouTube here. I am talking about sites that stream a specific TV show or channel illegally. These types of sites might have malware as well.
One last thing to look out for when browsing is fake “download”, “play now”, “play”, etc buttons. Be really careful around these. Keep an eye out for these on sites that you particularly don’t trust. Also, while on the topic, don’t fall for the “Your computer is infected” ads or popups as well. These are usually a trick to get you to download a virus. If you see one of these and you are unsure, close it, then open up your virus protection software and run a scan. This will tell you if you are truly infected or not.
Be Careful When Downloading Programs or Files
There are many times when you really just need to download a program or file from the Internet. If you do this correctly, then there is no issue. However, the key here is that when you download something, make sure it is from a trusted source. Downloading software directly from the software manufacturers website is one good tip. For example, if you need to download iTunes, download it from Apple itself, not some third party distributor. The only time you should download from a third party site is when the site itself links to the third party site for the download.
Our Exclusive Multi Layered Security Service includes:
- A Stellar Anti Virus
- A Proactive Anti Malware Scanner
- Superior Spyware Detection
- Custom Browser Settings
For Only $79.00
By following the tips and advice above, hopefully you will never get a virus again.
Affordable Computer Repair in Baltimore Maryland – Connected PC Solutions computer repair in Perry Hall, Maryland
#BaltimoreCompterRepair, #PCRepairInBaltimore, #ComputerRepairBaltimore
What is Spam? Tips and Recommendations
Junk e-mail is called Spam. Spam is usually defined as “mass produced unsolicited e-mail” or “mass produced unsolicited commercial e-mail.” In other words, it is junk mail.
Some Internet Providers now have anti-spam programs built into their service. They are not perfect, but they work fairly well. You can also get an anti-spam program for your computer, but unfortunately I don’t have any experience with them, so I can’t recommend any. You can also build your own anti-spam filters in most e-mail programs, but this can be quite complex for beginners, and usually they don’t stop that much spam. We suggest Vipre Internet Security which has the ability to not only check your email but your Facebook page as well for malicious content.
Most spam messages contain scams, pornography, hoaxes, viruses, or similar things. It is strongly recommended that you do NOT open these. Also, We highly suggest that you should NEVER reply to them, because it verifies that your address is valid.









You must be logged in to post a comment.